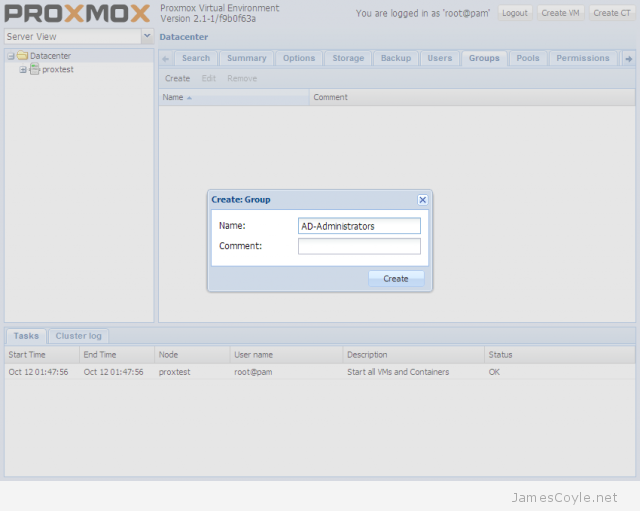
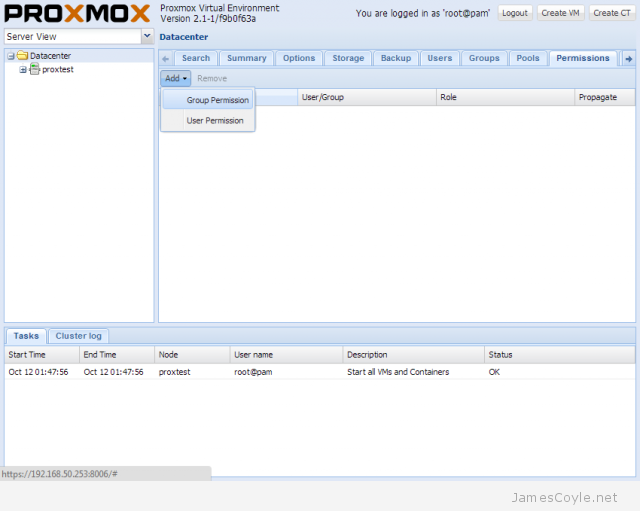
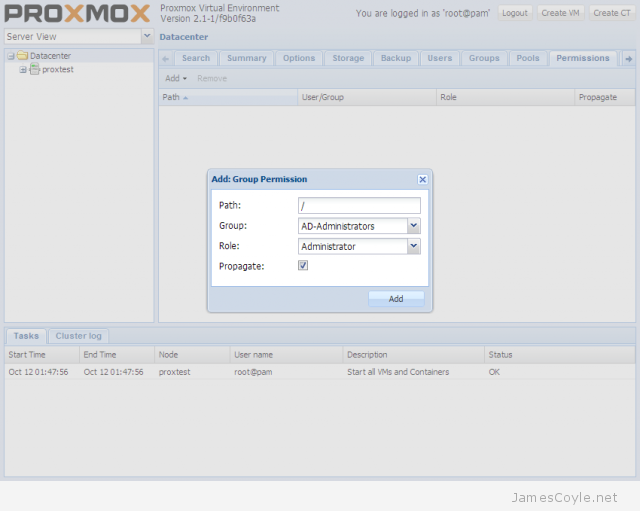
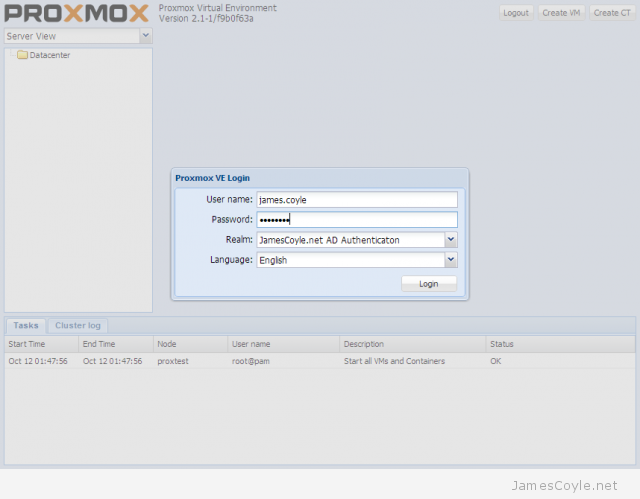
Proxmox has a test repository (repo) which can be used to deliver the latest software and updates using apt-get or aptitude.
This repo contains test software which the Proxmox dev team are currently working on and as such may contain bugs, be feature incomplete or contain security vulnerabilities. This is not recommended for production Proxmox servers and should be kept to your development/ test servers.
Login to your Proxmox console as root either using the web GUI console or directly via ssh.
Using vi, edit the apt sources file
vi /etc/apt/sources.list
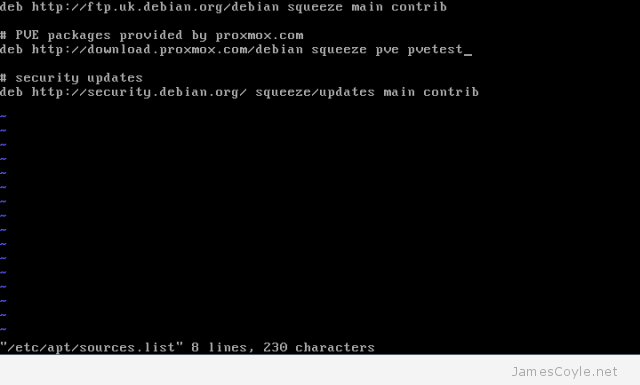
Find the line which contains deb http://download.proxmox.com/debian squeeze pve and append pvetest so that it looks like the below image.
Run the following command to update apt-get with the latest repository
aptitude update
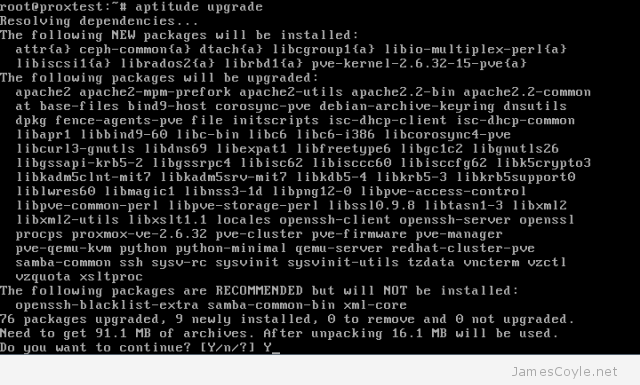
And finally to upgrade your system to the latest test version, run the upgrade command and type y.
aptitude upgrade
To remove the pvetest repository, simply edit the /etc/apt/sources.list file and remove the pvetest repo which you just added. Then run aptitude update.