Proxmox 3.1 package/ updates manager
Category : How-to
 Proxmox version 3.1 made a huge change to the way updates are managed. Prior to version 3.1, updates for the PVE software were managed from two main repositories – test and production – both of which were free and available. Generally the production repositories were used to ensure a stable and secure Proxmox host. These two repositories have now changed to the following:
Proxmox version 3.1 made a huge change to the way updates are managed. Prior to version 3.1, updates for the PVE software were managed from two main repositories – test and production – both of which were free and available. Generally the production repositories were used to ensure a stable and secure Proxmox host. These two repositories have now changed to the following:
Please note, this also works for version 4.x.
None subscription repository
This repository remains free, and all the code is still under AGPL v3. I believe this repository is similar to what the test repository used to be – containing test and potentially buggy packages. There is also the standard Debian repository for all other, non-Proxmox, updates. As these packages are potentially unstable, it is not recommended to use this repository for a production server.
Proxmox Version 3.x
Proxmox version 3.x is based on Debian Wheezy.
deb http://ftp.uk.debian.org/debian wheezy main contrib
deb http://download.proxmox.com/debian wheezy pve-no-subscription
Proxmox Version 4.x
If you run version 4.x of Proxmox, based on Debian Jessie then you’ll need to adjust the URL slightly as below:
deb http://ftp.uk.debian.org/debian jessie main contrib
deb http://download.proxmox.com/debian jessie pve-no-subscription
Enterprise repository
This repository requires a subscription license key to be added to Proxmox before you can access it. These packages are stable and are recommended for any production Proxmox server after version 3.1.
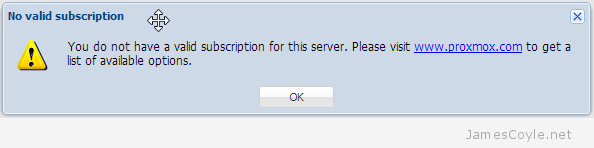
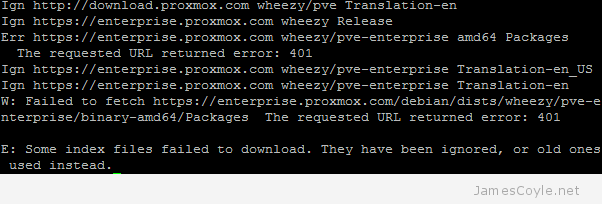
If you do not have a valid subscription, you will need to remove this repository otherwise apt-get will never complete it’s update. Without a valid subscription, you will see errors such as “You do not have a valid subscription for this server. Please visit www.proxmox.com to get a list of available options.”
To remove the repository, open the source list file in the apt-get sources folder
vi /etc/apt/sources.list.d/pve-enterprise.list
And comment out the line with a # as below.
#deb https://enterprise.proxmox.com/debian wheezy pve-enterprise
All updates will now come from the none subscription repository which are publicly available. Unfortunately, each time you click the Refresh button on the Updates tab you will receive the above message. You will also receive this message when you login to the web GUI.
What about the old updates repository?
The original updates repository should be removed once you have upgraded to Proxmox 3.1. No future updates will be available in this repository.
Edit the sources list and comment out the old repository:
vi /etc/apt/sources.list
If you used the test repository, you will need to comment that out too.
# PVE packages provided by proxmox.com #deb http://download.proxmox.com/debian wheezy pve
How to remove the “No Valid Subscription” message
Each time you log into Proxmox 3.1 a dialogue box pops up reminding you that you have not purchased a valid subscription. One way to remove the message is to purchase a subscription from the Proxmox team. Another method is to make a slight change to the code to remove the dialogue box from appearing.
See my post on how to change the code to remove the dialogue box.
 If you need a software firewall to shield containers on a Proxmox stack, you should always use a firewall on the host to decide what traffic is allowed for each container. This brings some obvious benefits such as it’s centrally managed – one configuration location for all containers on the node, and security as a compromised container cannot change firewall settings.
If you need a software firewall to shield containers on a Proxmox stack, you should always use a firewall on the host to decide what traffic is allowed for each container. This brings some obvious benefits such as it’s centrally managed – one configuration location for all containers on the node, and security as a compromised container cannot change firewall settings.